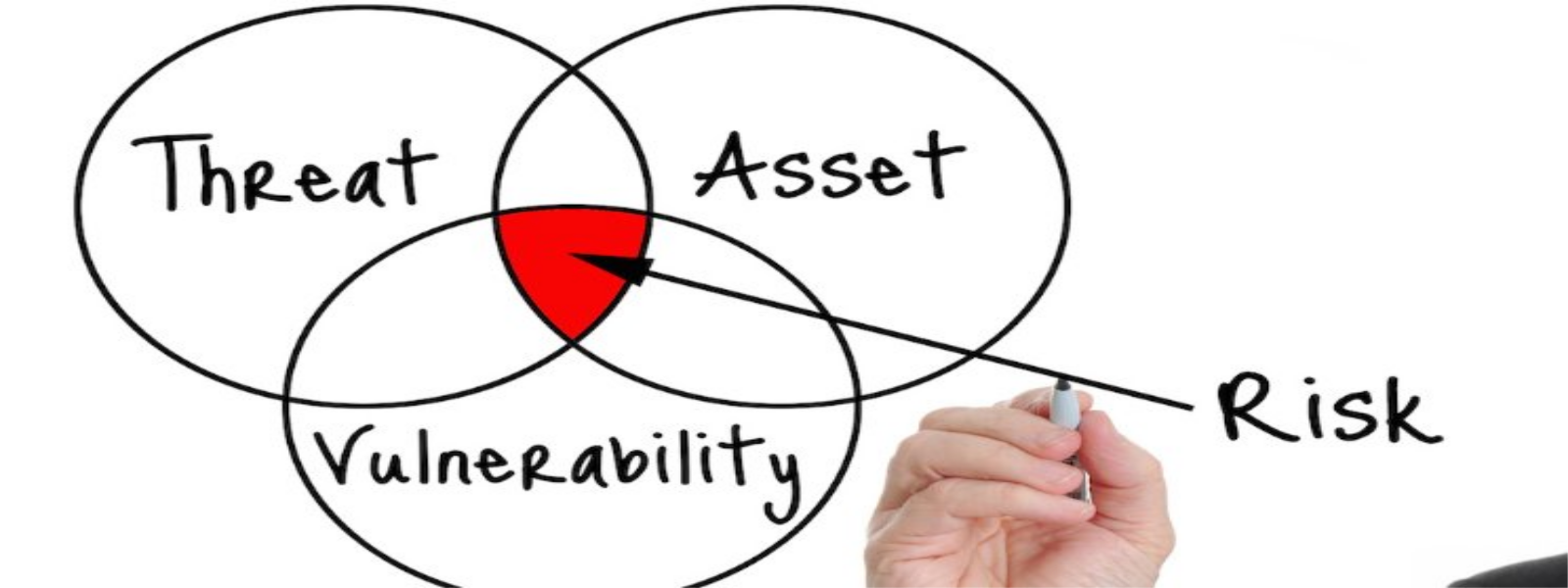
Cyber Risk Assessment
 Cyber risks are strategic business risks; it is not a IT issue. Management shall manage cyber risks with due care as Cyber security risks are a constantly evolving threat to an organization’s ability to achieve its objectives and deliver its core functions. Protecting key information assets is of critical importance to the sustainability and competitiveness of businesses today. Organizations need to be on the front foot in terms of their cyber pre-paredness. Organizations benefit from managing risks across their organizations; drawing effectively on senior management support, risk management policies and processes, a risk aware culture and the assessment of risks against objectives.
Cyber risks are strategic business risks; it is not a IT issue. Management shall manage cyber risks with due care as Cyber security risks are a constantly evolving threat to an organization’s ability to achieve its objectives and deliver its core functions. Protecting key information assets is of critical importance to the sustainability and competitiveness of businesses today. Organizations need to be on the front foot in terms of their cyber pre-paredness. Organizations benefit from managing risks across their organizations; drawing effectively on senior management support, risk management policies and processes, a risk aware culture and the assessment of risks against objectives.
Benefits in adopting a risk management approach to cyber security
Strategic Benefits
Strategic Benefits
Corporate decision making is improved through the high visibility of risk exposure, both for individual activities and major projects, across the whole of the organization.

Financial
Financial
Providing financial benefit to the organization through the reduction of losses and im-proved “value for money” potential.

Operational
Operational
Organizations are prepared for most eventualities, being assured of adequate contin-gency plans.
GAP Assessment
A gap assessment to compare your organization’s current security stance to the detailed recommendations against reference standard’ Security Controls is performed. This assessment is carried out through a series of collaborative interactions with key stakeholders, interviews with network and security staff, and in-depth re-views of your organization’s security architecture, processes, procedures and policies.
This assessment type determines what has been implemented and where gaps remain for each control and sub-control. Any gaps are identified, documented, and prioritized. Our services help to secure your organiza-tion’s environment and improve compliance by providing a comprehensive assessment of each important as-pect of your organizations’ security program to include but not limited to:
Internet Controls
External Controls
Physical Security
Policies & Procedures
Vulnerabilities & Threats
Reporting and Deliverables
At the conclusion of the assessment, we provide a comprehensive and detailed oriented post assessment re-port that clearly identifies your organization’s current state of implementation and compliance with the reference framework Security Controls. Additionally, this report provides a framework for a path forward to ongoing risk reduction with inclusion of the following items:
An executive overview summarizing the scope and outcome of the assessment
Methodology detailing the extent of the assessment performed and the tools used
The organization’s overall strengths and weaknesses identified during the assessment
Detailed findings and recommendations for controls.
Risk prioritized mitigation and remediation recommended actions
Risk versus effort analysis of proposed remediation actions for project planning
Proposed enhancements to business practices that will further strengthen the organization’s risk posture
Identifies gaps that exist between security efforts and business objectives